I’ve been looking into… er alright, let’s be honest, nerding out, to CIS’s top 20 risk framework. A set of scalable data-driven guidelines to ensure an org’s security.
I never said I wasn’t a nerd, ok. deal with it.
Most Risk frameworks yammer on for about 60 pages before getting to anything actionable
CIS is what PCI-DSS standards are derived from. They go from simple to really granular for every.single. system. You can use their guidance to secure just about any system, OS, device, etc.
The top 6 are the ones I think everyone should at least take a stab at.
I know. You’re sitting there waiting for the matrix. I won’t keep you waiting:
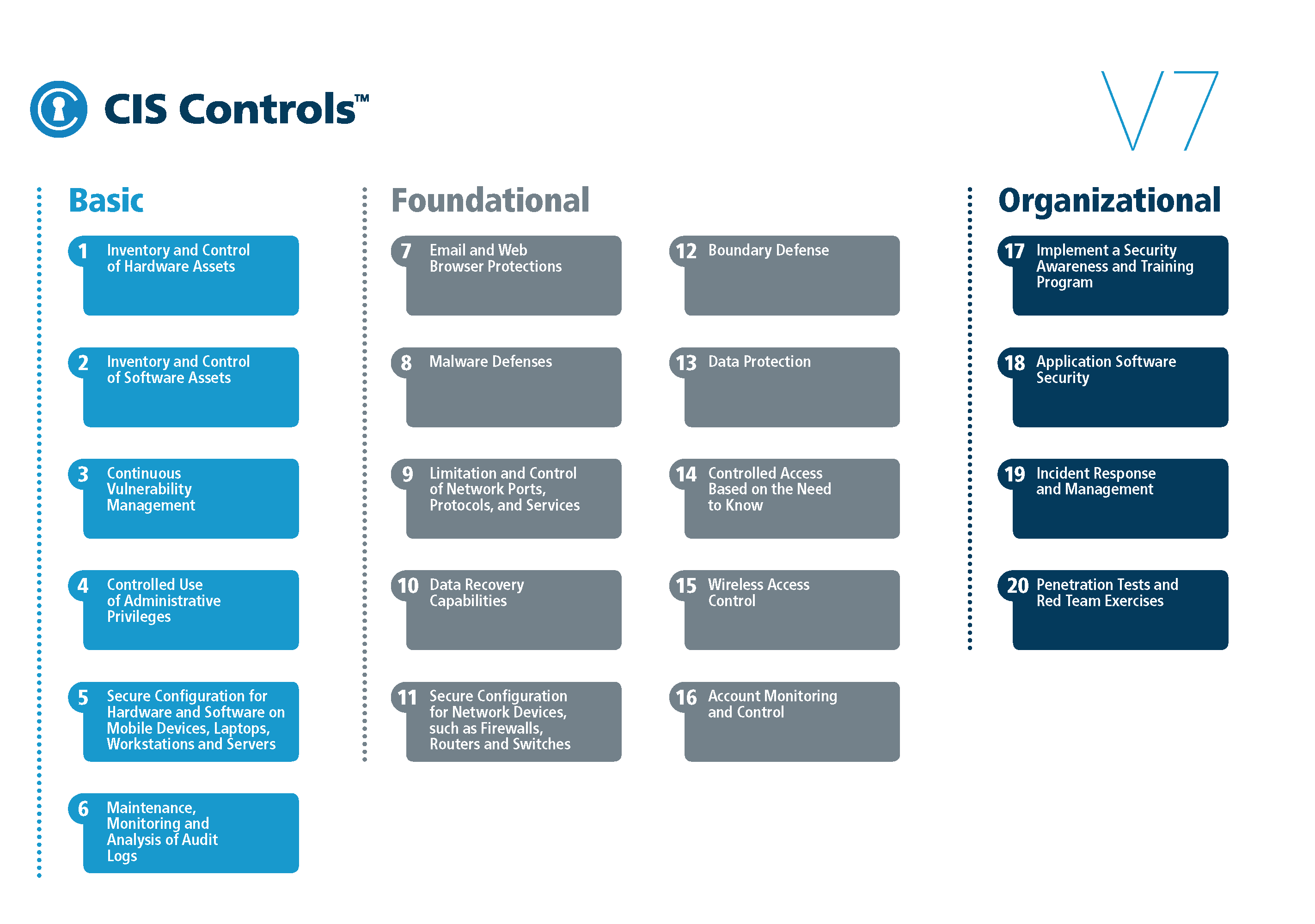
The longer version I formatted up a bit:
Pitching the six.
CIS Control 1: Inventory of Authorized and Unauthorized Devices
It’s impossible to protect devices you don’t know about. “If you can’t see it, you can’t protect it.”
-
Identify all devices
-
Document the inventory
-
Keep the inventory current
CIS Control 2 : Inventory of Authorized and Unauthorized Software
Inventory management can be challenging for any organization, but you can’t protect your systems unless you know what’s running on them. Not only helps security but gives increased visibility too.
-
Identify and document all software
-
Develop a whitelist of approved software
-
Manage the software on the system through regular scanning and updates
CIS Control 3 : Continuous Vulnerability Management
Continuously acquire, assess, and take action on new information in order to identify vulnerabilities, remediate, and minimize the window of opportunity for attackers.
-
Run Automated Vulnerability Scanning Tools
-
Perform Authenticated Vulnerability Scanning
-
Protect Dedicated Assessment Accounts
-
Deploy Automated Operating System Patch Management Tools
-
Deploy Automated Software Patch Management Tools
-
Compare Back-to-Back Vulnerability Scans
-
Utilize a Risk-Rating Process
CIS Control 4 : Controlled Use of Administrative Privileges
The processes and tools used to track/control/prevent/correct the use, assignment, and configuration of administrative privileges on computers, networks, and applications.
-
Maintain Inventory of Administrative Accounts
-
Change Default Passwords
-
Ensure the Use of Dedicated Administrative Accounts
-
Use Unique Passwords
-
Use Multi-Factor Authentication for All Administrative Access
-
Use Dedicated Workstations for All Administrative Tasks
-
Limit Access to Script Tools
-
Log and Alert on Changes to Administrative Group Membership
-
Log and Alert on Unsuccessful Administrative Account Login
CIS Control 5 : Secure Configurations for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers
Establish, implement, and actively manage (track, report on, correct) the security configuration of laptops, servers, and workstations using a rigorous configuration management and change control process in order to prevent attackers from exploiting vulnerable services and settings.
-
Establish configuration baselines
-
Create standard images of operating systems and software applications
-
Store master images of the systems
-
Consistently manage and update the systems
-
Deploy system configuration management tools
-
Implement automated configuration monitoring systems
CIS Control 6 : Maintenance, Monitoring and Analysis of Audit Logs
Collect, manage, and analyze audit logs of events that could help detect, understand, or recover from an attack.
-
Utilize Three Synchronized Time Sources
-
Activate Audit Logging
-
Enable Detailed Logging
-
Ensure Adequate Storage for Logs
-
Central Log Management
-
Deploy SIEM or Log Analytic Tools
-
Regularly Review Logs
-
Regularly Tune SIEM