Inherent risk refers to the inherent risk inherent in a business or financial activity. This type of risk is present in every business or financial activity, regardless of whether it is a large corporation or a small business. Inherent risk can be caused by a variety of factors, such as the nature of the business, …
Author: ModeratelyAwesome
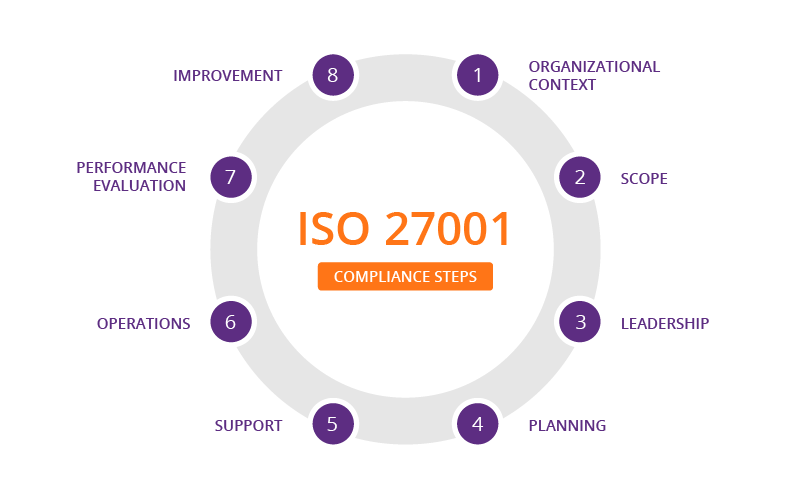
Doing ISO 27001 isn’t just following a few NIST principles (handy list inside!)
This list linked below is awesome. It doesn’t seem to be common knowledge on what it covers and how much (i.e., A LOT). Loving the clarity here. Fun fact: ISO tells you *what* to do but not *how* to do it for most items and that’s intentional. You define that for your business/use case. It’s …

Chaos Engineering?
Why haven’t I heard of this sooner? Fascinating! Apparently Netflix started Chaos Monkey, a tool to test your infrastructure. It randomly terminates one system or something random in your environment. You get to deal with the ensuing ‘chaos’ to see how well you find it, recover, etc. Sounds like it’s a mature tool for a …
CIS Controls – The top 6 are a good start
I’ve been looking into… er alright, let’s be honest, nerding out, to CIS’s top 20 risk framework. A set of scalable data-driven guidelines to ensure an org’s security. I never said I wasn’t a nerd, ok. deal with it. Most Risk frameworks yammer on for about 60 pages before getting to anything actionable CIS …

Audit once – Use a Bunch – SOC Reports (SSAE18) Simplified!
I see a fair amount of confusion from Security Professionals to Auditors and beyond. I’ll try to simplify it here. SOC – Service Organization Controls And I see people confidently speaking about it and they’re wrong. Let’s fix that! All the things I see are in Auditor-ese, lets simplify it! There’s 3 SOC reports. Click …

How to find outside email forwarding in Office 365 using Powershell
Hi there! Have you ever tried doing simple stuff in Office 365 as an Email Administrator like ya know.. find out how many people have their work email forwarded to outside email addresses? Simple? Not exactly. Don’t worry, we got this. There’s lots of awesome things you can do with Windows Powershell and 365 remotely, it turns out. …

Wanna know how to get a Security professional to make the stink face?
Say Security and WordPress in the same sentence. They’ve seen at least one (or more) hacked sites in their time. For good reason. It happens a lot. They might even look like they need a squish ball for the stress you’ve just brought upon them. But why? Is it because WordPress isn’t secure? …

What’s PCI-DSS? tl;dr it!
PCI-DSS stands for Payment Card Industry – Data Security Standard PCI is a council of all the credit card companies that gathered together to create common security standards to adhere to (e.g., Visa, Mastercard, Discover, American Express). They cover credit card information and PII storage (Personally Identifiable Information). You either have to select …

What’s the difference between IT Compliance and IT Audit?
I’ve looked all over and have yet to find a clear and simplified explanation on this. I see why people are confused. Let’s clear it up. Here goes: IT Compliance – Short Answer: What controls should we have in place? Future. Longer answer: IT Compliance asks bigger questions about what should happen and works to …